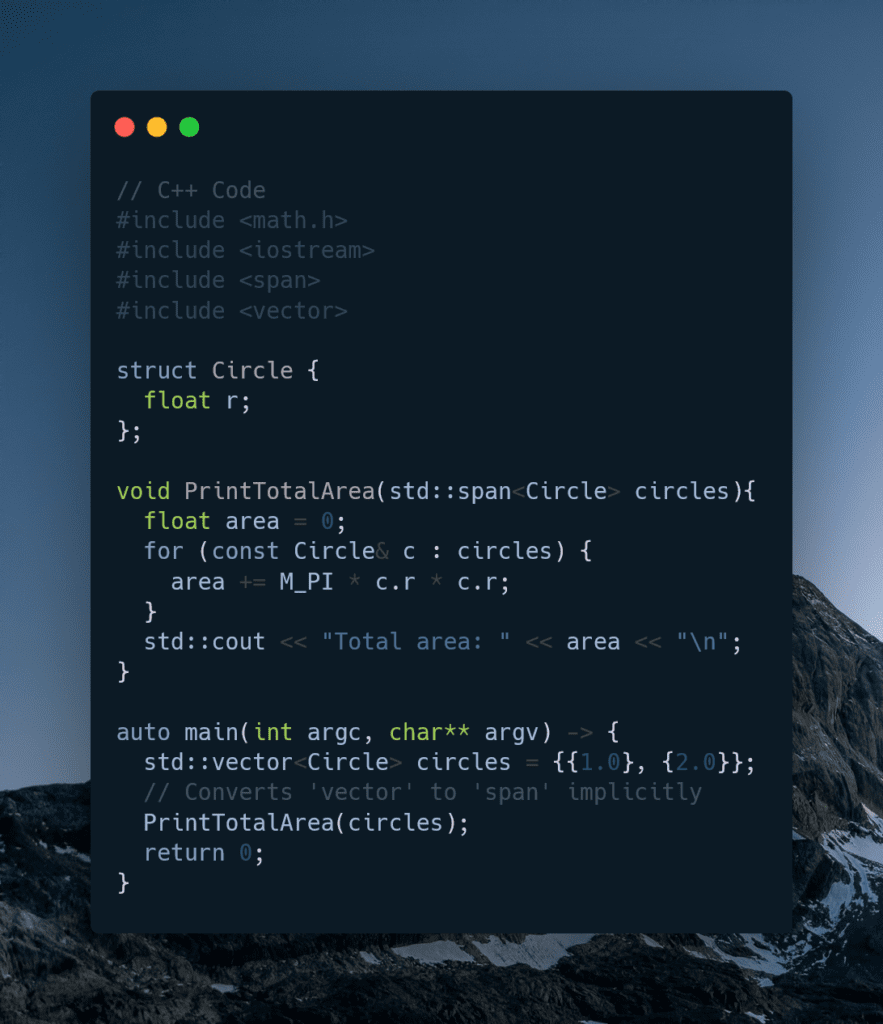
When typing, it’s always disconcerting to realize THAT CAPS LOCK IS ON. Caps Lock is useful (sometimes), but more often than not I find myself accidentally engaging it. However, you can change things around in your preferred OS (this guide is for Windows) to allow disabling Caps Lock with Shift. This simple setting changes things for the better, and makes more logical sense.
We’ve Been Doing It Wrong
The logical argument for disabling Caps Lock with Shift boils down to states, and being aware of the key’s current state with the least amount of information possible.
If Caps Lock is a toggle, it’s possible to accidentally hit the key an unknown number of times, or lose track of whether it’s on or off. In order to discover the ‘state’ of the key, you must begin typing. The other way to discover the ‘state’ would be to glance down at your keys, or have some other sort of ‘indicator’ like a keyboard implements visually or graphically. Both of these are wasted efforts and time.
When typing, you shouldn’t look at the keys as much as possible. The cleaner way to handle our problem then is to make Shift disable Caps Lock. When you start typing your sentence, if caps lock is on, it’s naturally disabled. It works naturally with how you type and I no longer encountered any errors with Caps Lock at all upon integrating this. When you need to use it, turn it on. Then, go back to typing as before. It’s no longer a separate mechanism to keep track of, but integrated into the typing experience and bows out quickly after usage without any extra key press. As an added bonus, you don’t have to wonder if Caps Lock is ON either. You simply click it, and type. If it was on, no effect!
To learn how to enable this glorious setting, just read on. Or, if you’re using Linux, this will get that Google search (or DuckDuckGo) started for you. 🙂
Windows 10
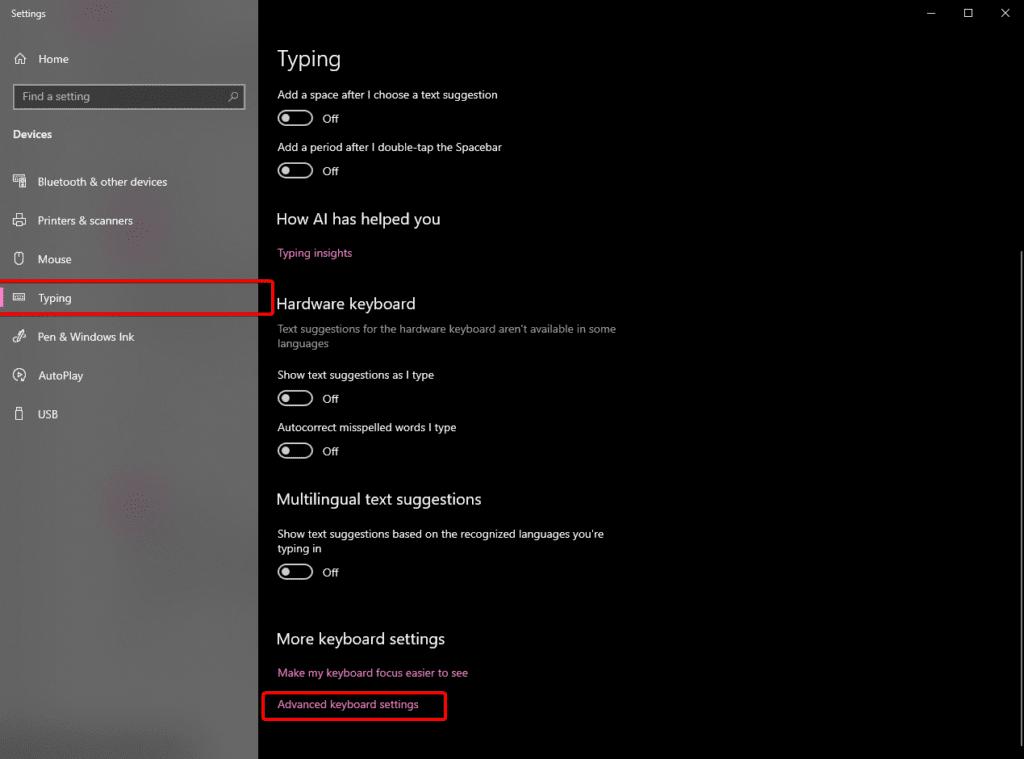
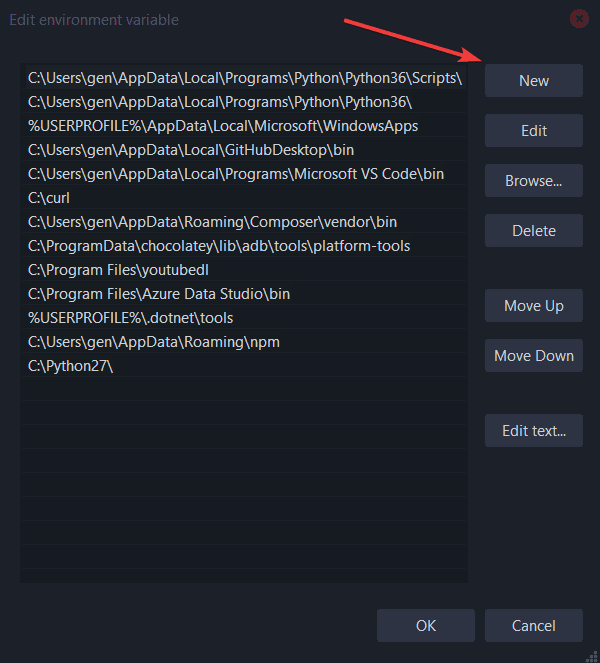
- Visit Settings > Typing > Advanced keyboard settings
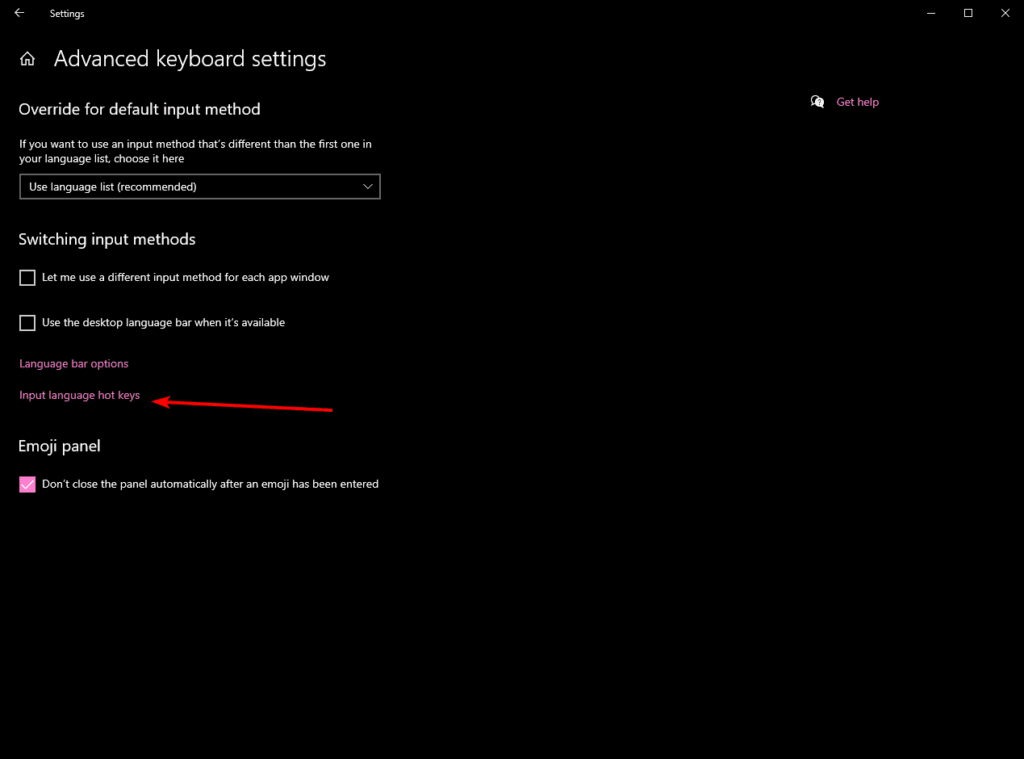
- Then find Input language hot keys
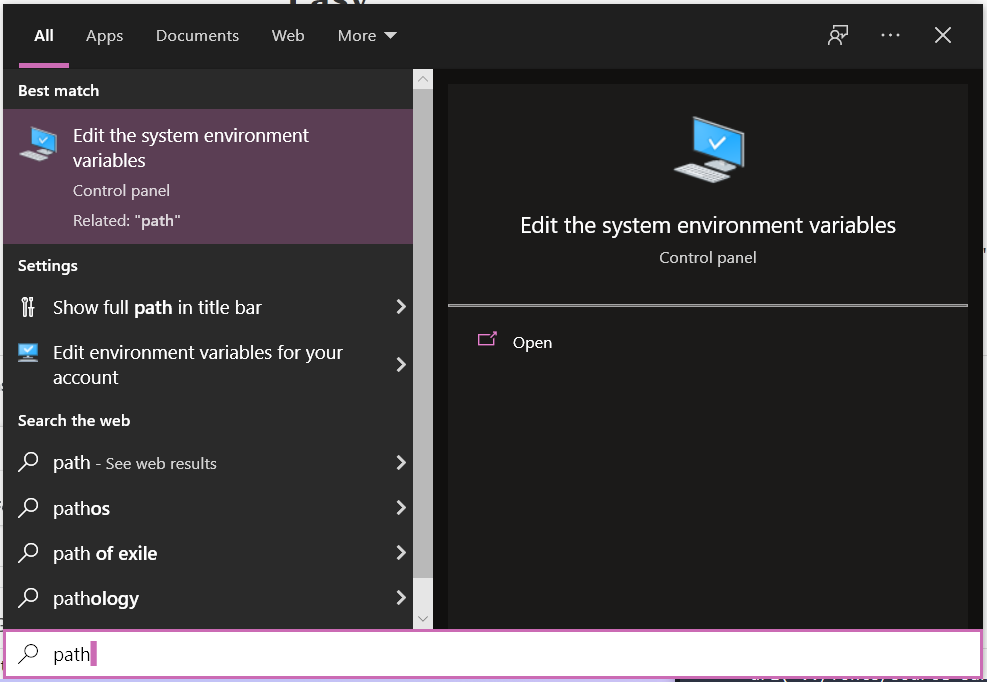
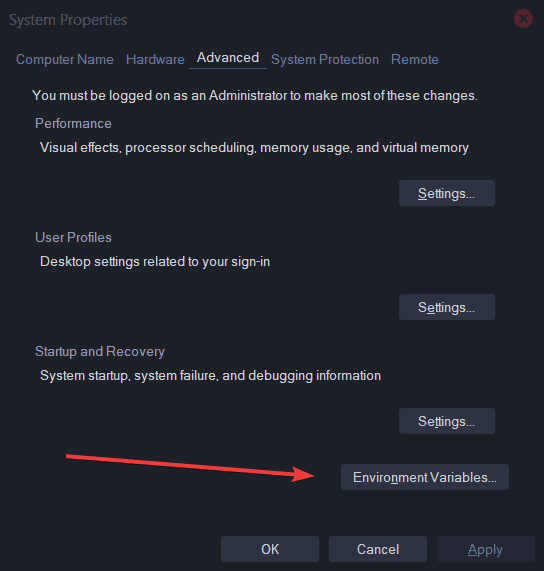
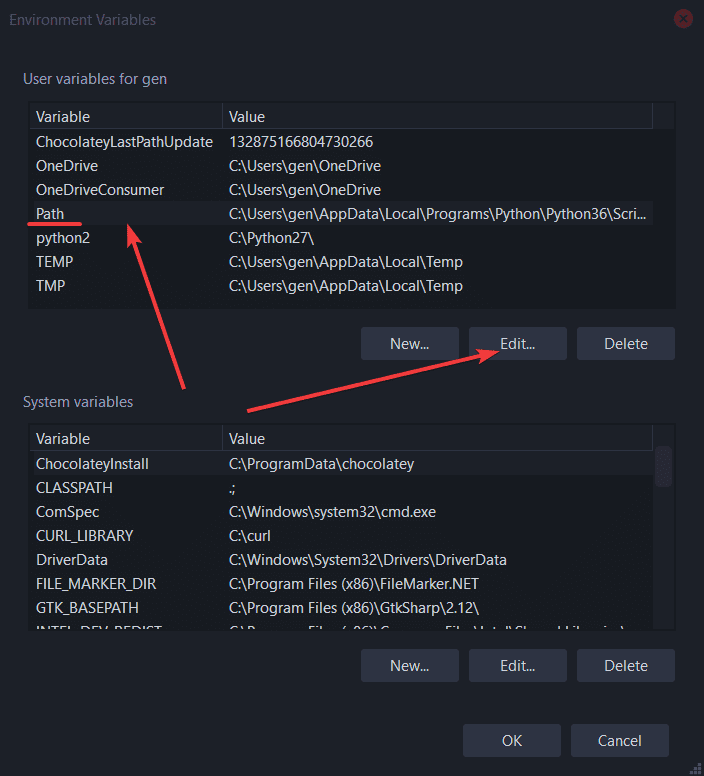
- From there you will see the very last image’s menu
Windows 11
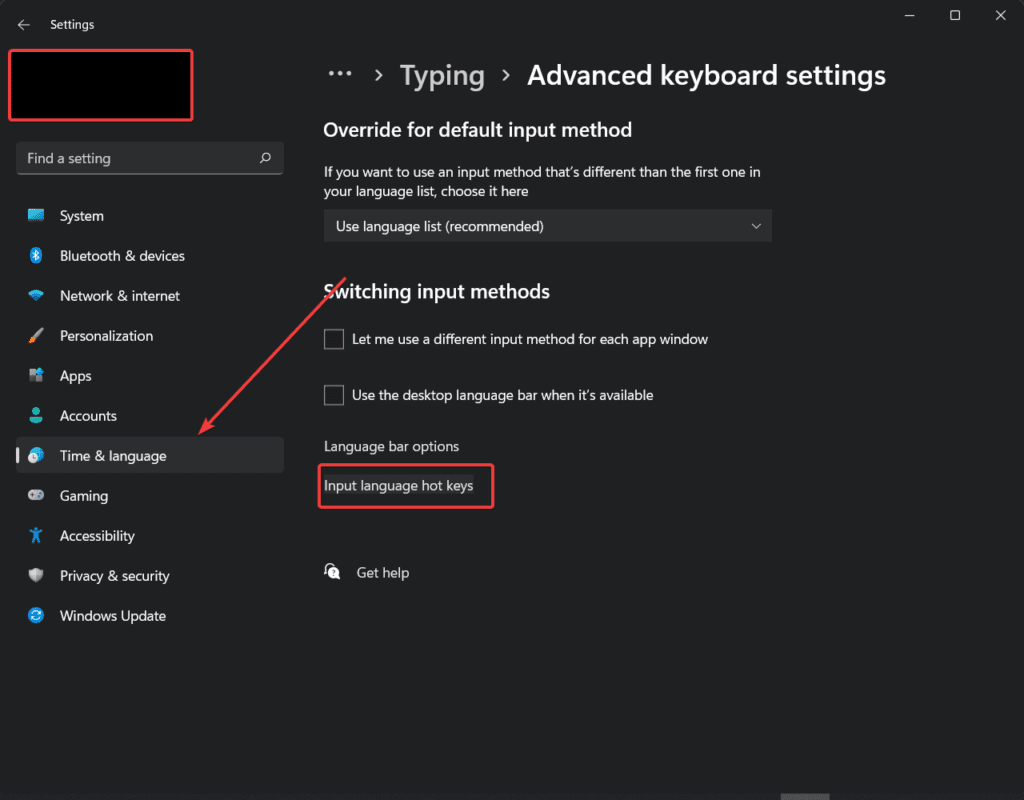
- Navigate to Time and Language > Typing > Advanced keyboard settings
- Find Input language hot keys
- You will see the very last image’s menu
You will then want to change this option:
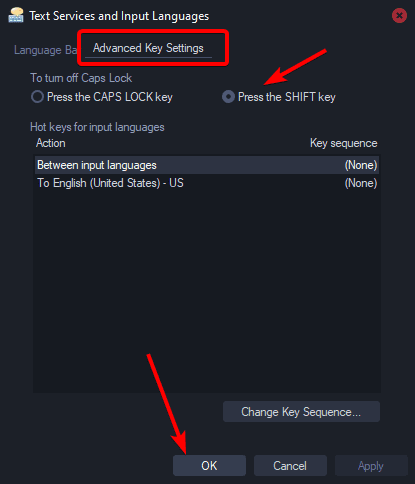
Now I can’t go back, and I never wonder or think about caps lock accidentally being on. Been using this as default for around five years now. It surprises me this isn’t the de facto setting.
It helps me if you share this post
Published 2022-08-19 07:05:33